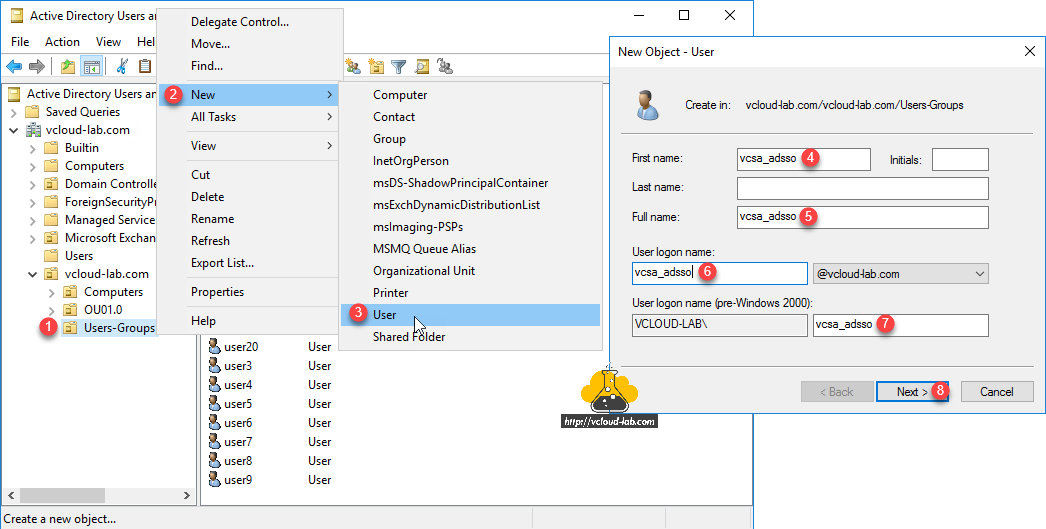
I have already written a article on Add a vCenter Single Sign On Identity Source Active Directory (Windows Integrated Authentication), there are 2 ways to configure vCenter SSO with Windows Integrated Authentication, In the earlier article I have shown how to Use Machine Account, and the settings doesn't require much settings on active directory side, but the requirement is the domain account you want to use for SSO, you must be logged with same user account onto your computer OS and then perform the steps. But most of the time you might require to use separate service account, that time you use another method Service Principal Name (SPN). Before processing first I will create one service user account with name vcsa_adsso on the Active directory.
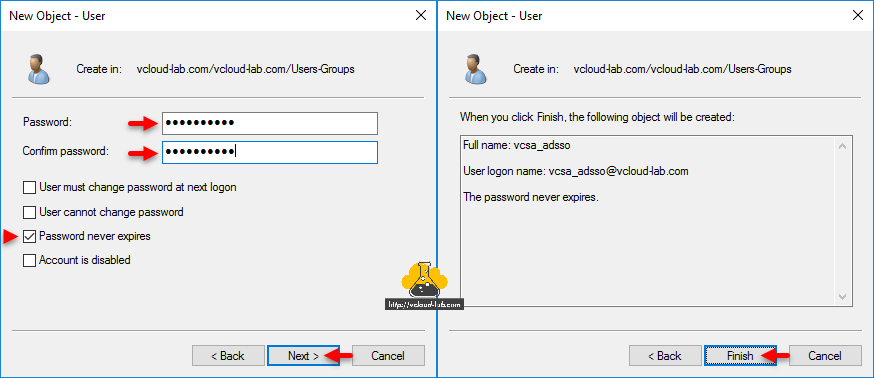
Make sure Password never expires on the new service account.
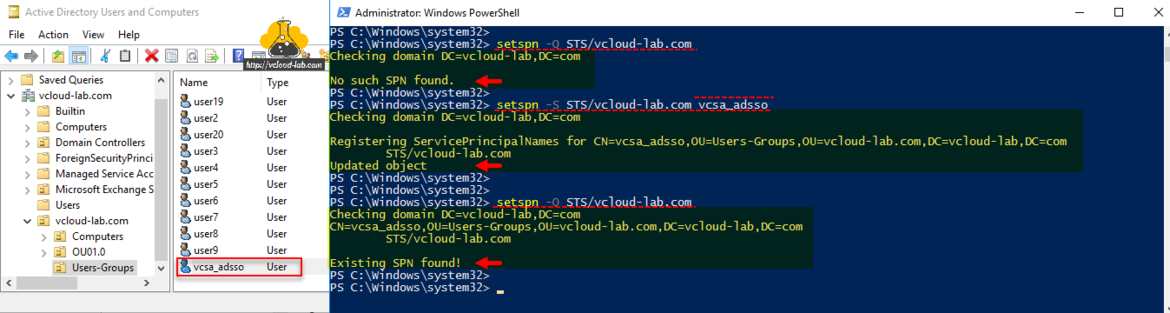
Once the user account is created, I will require a SPN (Service Principal Name) for the same service user account. A service principal name (SPN) is a unique identifier of a service instance. SPNs are used by Kerberos authentication to associate a service instance with a service logon account. This allows a client application to request that the service authenticate an account even if the client does not have the account name. In the first command I will check if there is any SPN exists for the account, I don't have any SPN created.
setspn -Q STS/vcloud-lab.com
Next create/register a SPN object for the service user account, This step requires you to open command prompt as administrator. Once SPN is registered verify SPN exist in the list.
setspn -S STS/vcloud-lab.com vcsa_adsso
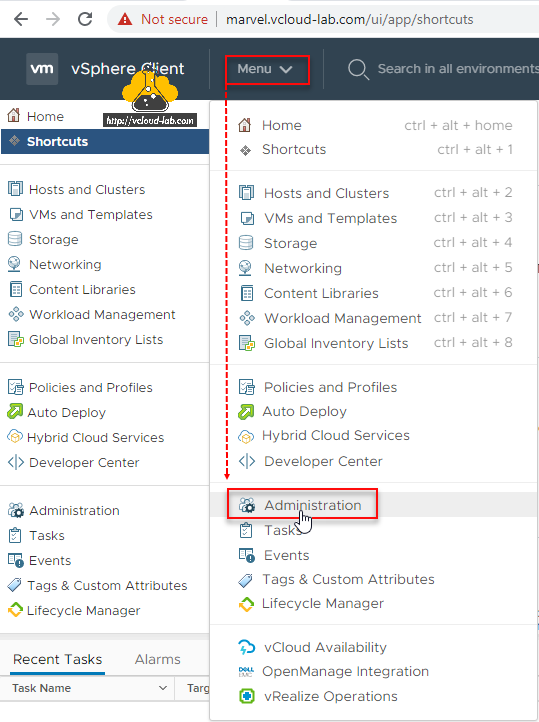
On the vSphere Client, go to Menu and click Administration from the list.
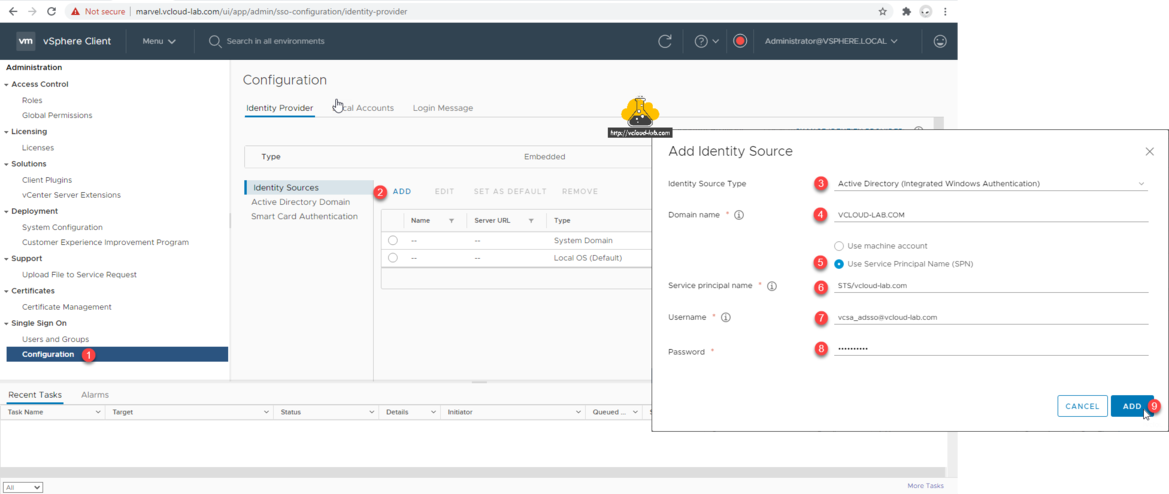
Under the Single Sign On, click Configuration, then click Add on Identity Sources. On the new Add Identity Source box, fill up below information.
Identity Source Type: Active Directory (Integrated Windows Authentication)
Domain name: Your domain name. Example - vcloud-lab.com
Use Service Principal Name (SPN)
Service Principal name: STS/DomainName. Example - STS/vcloud-lab.com
Username: Username as in email format. Example - vcsa_adsso@vcloud-lab.com
Password
Click Add button.
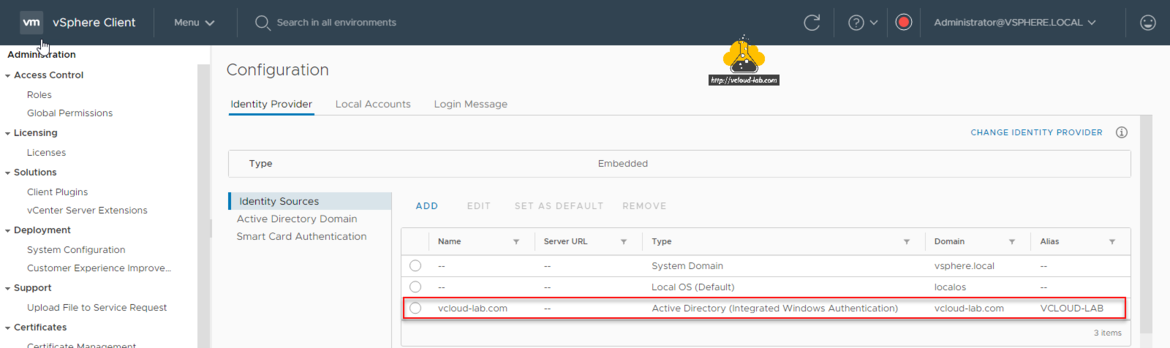
If the configuration is successful you will see new Identity source provider (Type Active Directory (Integrated Windows Authentication)) in the list.
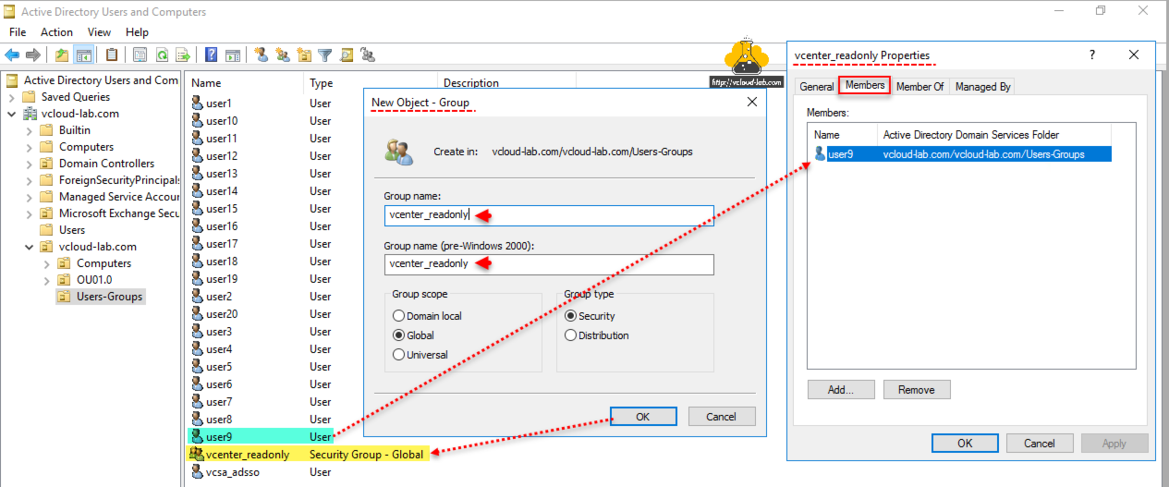
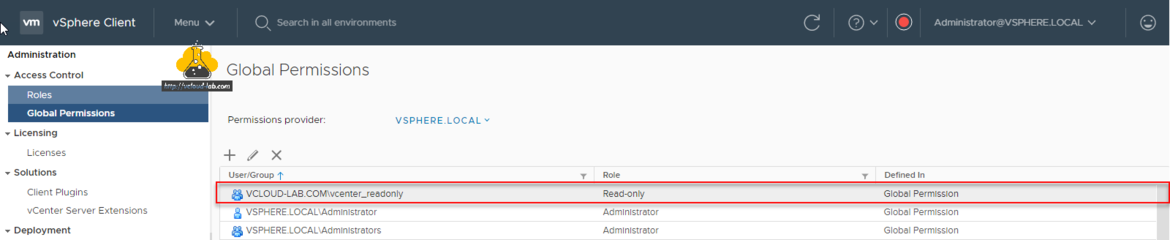
In the next process, On my Active directory I have created a one Group and added a user as members to it, I will provide this group read only permissions on the vCenter server.
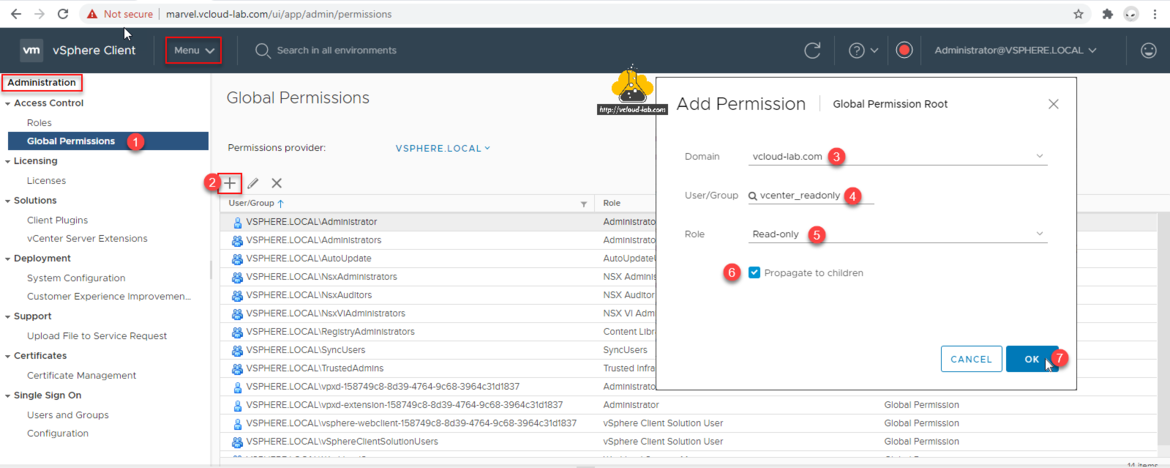
On the vCenter go to Menu >> Administration expand Access Control then choose Global Permissions, Click + plus button to Add Permission, Change Domain from list, search for the User/Group and choose role, If required Propagate to children, (This is Global Permission on the Root), Click OK button.
Verify new read-only permission added to a group.
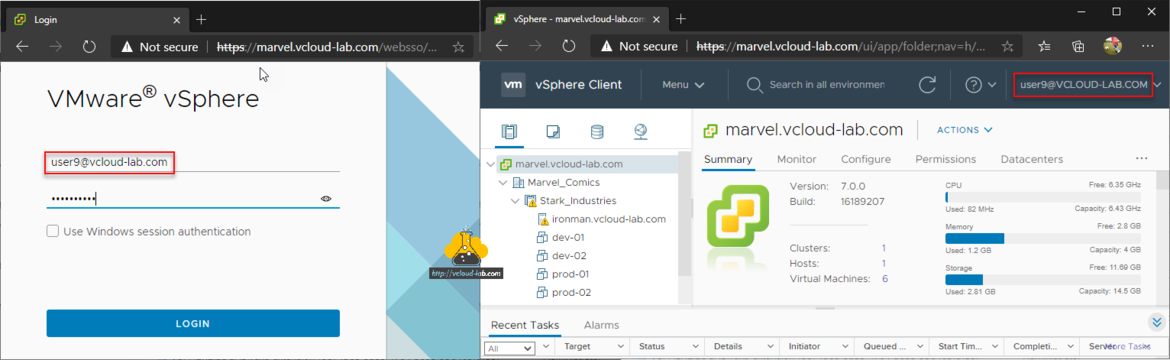
Now verify logging with the username, I am using either incognito mode or other browser and testing if it is successful, It is working good.
Useful Articles
ADDING AND CONFIGURING VMWARE VSPHERE VCENTER SSO ACTIVE DIRECTORY AS LDAP SERVER
VMWARE SECURITY BEST PRACTICES: POWERCLI ENABLE OR DISABLE ESXI SSH
vSphere ESXi security best practices: Time configuration - (NTP) Network Time Protocol
Configure syslog on VMware ESXi hosts: VMware best practices